SLAA547C July 2013 – July 2021 MSP430FR5739
4.1.3 Substitute Bytes (Subbytes Operation)
The Subbytes operation is a nonlinear substitution. This is a major reason for the security of the AES. There are different ways of interpreting the Subbytes operation. In this application report, it is sufficient to consider the Subbytes step as a lookup in a table. With the help of this lookup table, the 16 bytes of the state (the input data) are substituted by the corresponding values found in the table (see Figure 4-3).
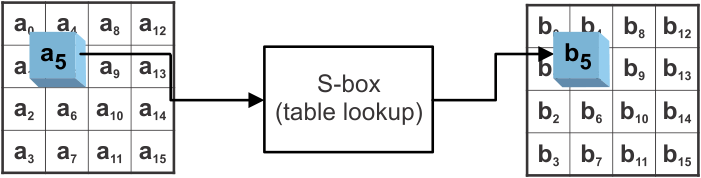 Figure 4-3 Subbytes Operation
Figure 4-3 Subbytes Operation