SPRT788 May 2025 AM2612 , AM2612-Q1 , AM2631 , AM2631-Q1 , AM2632 , AM2632-Q1 , AM2634-Q1 , AM263P2-Q1 , AM263P4 , AM263P4-Q1
3 Device Lifecycle and Provisioning Flow
The flow is also explained in MCU+ Academy.
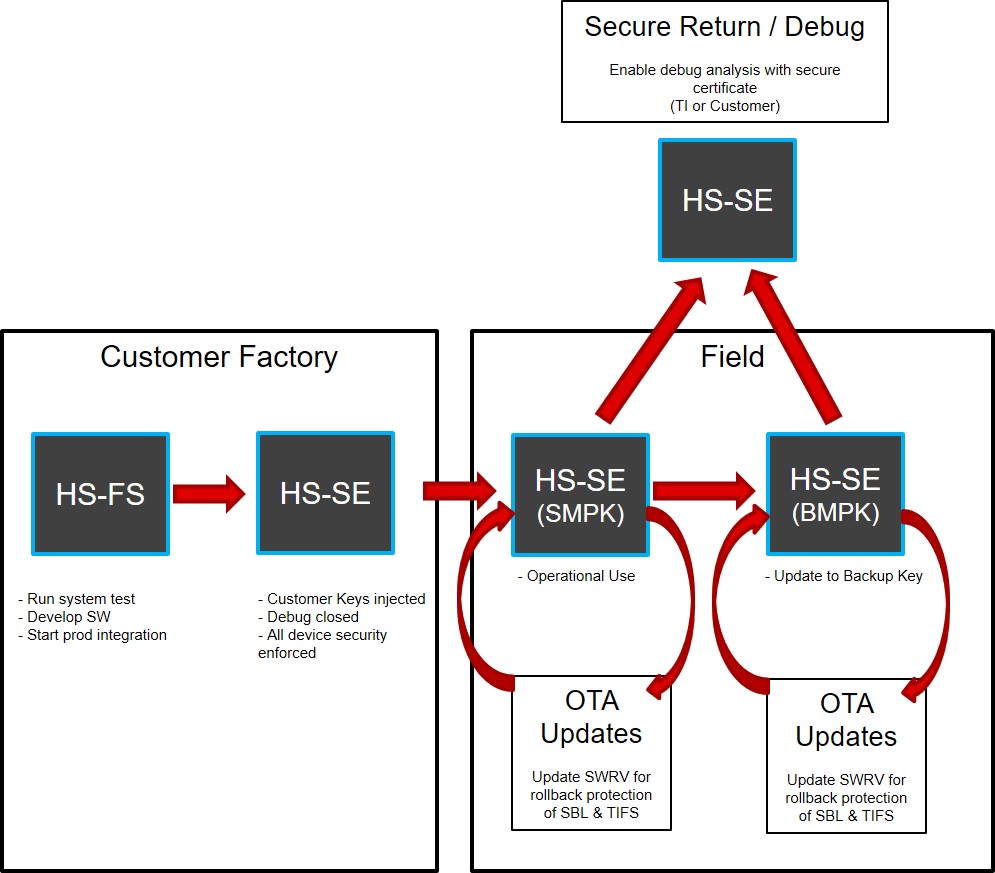 Figure 1 Secure Lifecycle of AM26x
Device Family
Figure 1 Secure Lifecycle of AM26x
Device FamilyStage 1:
User is delivered the device in HSFS (Field Secure) state. The device contains TI keys provisioned. In this state, the HSM core only executes a code which is encrypted and signed with TI keys.
Stage 2:
TI supports provisioning of user keys by using a key provisioning package (in a trusted environment), with user keys encrypted and signed using the TI keys. This key certificate is then securely transmitted using the SBL Key Writer example executing on the device available as part of OTP Key Provisioning Package. There are multiple ways of using SBL Key Writer, for example UART Boot Mode, Flash Boot Mode (QSPI or OSPI boot mode) and more. Confidentiality of the user keys is maintained throughout the process that allows user to replicate the process even in a non-secure environment. Once user encryption keys are provisioned, the life-cycle of the device is changed to HSSE state.
Stage 3:
Now as the device is in HSSE state for example, device with keys provisioned, secure boot enforced and debug interfaces locked, the application code can be programmed into the external flash (using the device, if required). The uniflash available as part of MCU+ SDK can be used to program the bootloader as well as application images into the external flash. Note, as the device is transitioned to HSSE, the provisioning process by uniflash images are also securely booted on the device. As the device supports encrypted secure boot, the data can be made encrypted over communication medium as well as external flash storage to maintain confidentiality.
The user code for example, HSM Run Time firmware and the SBL are encrypted and signed using the user keys that is available in the device secure storage. Once all the required images such as HSM Run Time software, SBL software and Application Images are provisioned the code is always a secure boot.