- Contact Us
- |
- TI Worldwide: United States
- |
- my.TI Login
|
THE INTERNET: WEBOLUTIONARY TECHNOLOGY EDI and the InternetBrett BatsonAbstract: A project with Avex Electronics demonstrates that cost savings of several orders of magnitude can be realized when using EDI over the Internet, compared to yearly VAN costs. The EDI Internet program needs several trading partners before the cost of the Templar™ SX software/maintenance is effective. However, cost is not necessarily the prime factor for using the Internet, according to Thomas St. Peter, TI’s worldwide EDI program manager. Rather, use of the Internet allows TI to broaden its markets both vertically and horizontally. The Templar SX product uses existing standards such as RSA cryptography, X509 key certificates, ISO 9735 EDI standards and MIME/EDI (RFC 1767) to address these issues. What follows is an example of the process involved in a trading partner sending an EDI order interchange to TI over the Internet and an acknowledgment returned by TI to the trading partner.
Electronic data interchange (EDI) offers exchange of business data directly between the computers of one or more trading companies. TI has been a leading light in the EDI industry since its inception for internal use more than 20 years ago. EDI is a “paperless” method of transferring such data as orders, forecasts, invoices and order responses. Some advantages are the elimination of data reentry with the consequent risks of copying errors; process speed also is improved. So, cost reductions can be realized. EDI’s success relies on the use of standardized formats that are recognized by the trading partners in an EDI relationship. Until mid-1996 the data was sent to and received by mainly third-party or value-added networks (VANs) for handling communications and mailboxes (Figure 1). The VANs use a traditional-store-and-forward concept of handling data. Rental fees are charged for use of an electronic mailbox to hold the data. Additional costs are levied for every message sent and retrieved from that mailbox, measured on a volume basis (i.e., the more data you deal with the more you pay). As the Internet matures as an alternative communications method, things are beginning to change. VAN connections for many trading partners are much slower than their Internet connections. One partner recently reported taking nearly two days to download approximately 3.5 MB of price catalogue data! “Imagine tripling your EDI volume, increasing your transmission speed 150 times, sending EDI documents over the same high speed digital network as your e-mail or binary files, having universal access to millions of potential customers and trading partners—and paying a fraction of your current costs for transmission.” If you read the previous paragraph you might be forgiven for taking those claims with a pinch of salt. The quotation comes from the Premenos web page regarding its Templar™ Secure Exchange (Templar SX) product for doing EDI over the Internet. The Templar SX product matches TI’s strategy to pursue an Internet solution, so TI obtained a license and tested the claims. This came to fruition in mid-1996 when a pilot system with Avex Electronics in the United States went live. Apart from minor teething problems and an issue with transfer of data between TI’s mainframe, (where the applications and EDI translation software reside) and the Templar SX product on a UNIX™ platform, the project has been very successful. Indeed, no errors in the process have been reported between September 1996 and the time of writing this article (April 1997) and this is with a flow of some 1300 documents a month. Based on this, U.S. EDI Operations has targeted six more trading partners to join the program this year. European EDI Operations based in Sunbury in the U.K. has obtained the “buy-in” of two large corporations and have had discussions with several others. Interest is very high. Because of U.S. government restrictions on levels of encryption, TI has purchased a second copy of the Templar SX license for international use outside the United States.
 Figure 1. Electronic data interchange The project with Avex has demonstrated that cost savings of several orders of magnitude can be realized when compared to yearly VAN costs. The EDI Internet program needs several trading partners before the cost of the Templar SX software/maintenance is offset. However, cost is not necessarily the prime factor for using the Internet, according to Thomas St. Peter, TI’s World Wide EDI program manager. Rather, use of the Internet allows TI to broaden its markets both vertically and horizontally. TI can broaden its markets horizontally because of the potential to reach small-and medium-sized enterprises that do not have nor want complex EDI/VAN, but who have Internet connections, experience and a level of comfort in using it. TI can broaden its markets vertically because once the Internet connection is established there is a base to extend TI’s presence. Design engineers, for example, would have the potential to exchange technical drawings. The impressive response times to date become crucial when one considers the businesses that are looking to “just-in-time” manufacturing concepts. For many semiconductor devices one is now seeing six-month product life cycles where only five years ago it was closer to two years. The ease and speed of setup of a communication link with a trading partner lends support to this move. Inevitably with the use of relatively new EDI technology problems and issues have arisen and are being addressed. These center around the following areas:
The Templar SX product makes use of existing standards such as RSA cryptography, X.509 key certificates, ISO 9735 EDI standards and MIME/EDI (RFC 1767) to address these issues. What follows is an example of the process involved in a trading partner sending an EDI ORDERS interchange to TI over the Internet and an acknowledgment returned by TI to the trading partner. EDI over the Internet model (Figure 2)Trading partner steps
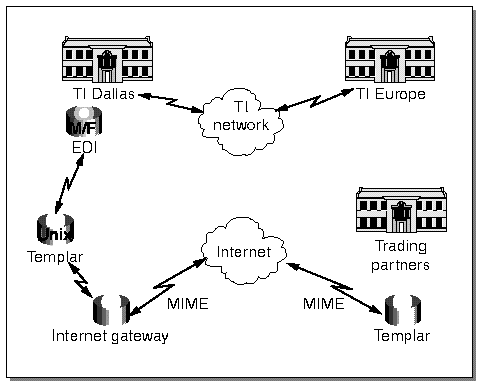 Figure 2. Internet EDI advantage
Texas Instruments steps (Figure 3)
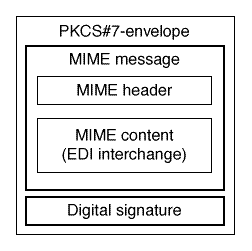 Figure 3. Internet EDI advantage
Trading partner steps
Templar Secure Exchange applicationsThe Templar SX software is divided into four applications: Trading partner profiles, Trading partner agree-ments, Key management and Tracking. Trading partner profiles. This application is used to create and maintain profiles and to bind a key to a profile. The profile contains several pieces of information to allow Templar SX to identify a trading partner and to process an EDI interchange. Also, the public key of a particular trading partner is linked or bound to that partner’s profile, allowing encryption, authentication and nonrepudiation security features to be used. Trading partner agreements. This application is used to create, view and maintain agreements. Those set up at TI and on the trading partner’s Templar SX must match. The agreement includes the send and receive policies where a number of parameters can be set. For instance, retransmission options can be set if an acknowledgment of data sent is not received within a given period. This could be automatic retransmission or simply e-mail notification to an operations group. Security features also can be set, including those to apply to outgoing data and those to expect on incoming data. For outgoing data there also are several transport options that can be selected. These include e-mail (the method chosen by TI), TCP direct to a trading partner’s Templar SX system, via a web interface to send data to a trading partner’s Internet web server, or via a file interface where data is saved to a file and sent to the trading partner by an agreed route. Key management. This application is used to create local keys, accept remote keys and maintain existing keys. TI and each trading partner need a key pair (public and private) to use Templar SX’s security features. An option within this application is to allow the public keys to be sent via e-mail to the various trading partners. Tracking. This application is used to track the status of both inbound and outbound events. This can be on two levels. The first is high-level information about the transmission and whether more than one EDI interchange has been sent or received. The second can show details of each EDI interchange, including whether the transmission was successful, date and volume information, e-mail addresses and security information. Within this application, transmissions can be set up for reprocessing and retransmitting after errors have been found.
SummaryThe use of Templar SX has allowed TI to be one of the first companies to explore the potential of batch EDI over the Internet. Security, authentication and nonrepudiation issues have been addressed and the use by Templar SX of standards, where these currently exist, will allow for compatibility with new products as they come onto the market. Savings in terms of speed and cost have been achieved, which helps bring about benefits to TI and its trading partners. Reliability and robustness also have been seen. A question sometimes raised over using the Internet in Europe for electronic trading is that it is less mature and reliable compared with North America. Only time will tell if this is still a valid argument as pilot programs begin with TI’s European trading partners. The move to use the Internet to carry out trade electronically using EDI is exciting. The Internet links also will be used to send other types of data such as technical drawings. FTP can be used to push data to clients, especially bulk data such as customized product price catalogues for distributors and product inventory reports. As issues such as security and authenticity become more understood and the software providing the necessary facilities to overcome these concerns becomes more prevalent, then we will see even greater use of the Internet and TI will continue to be at the forefront.
GlossarySingle-key cryptography—also known as symmetric-key cryptography. This is where both trading partners possess a single key to encrypt and decrypt the data. Public /private key cryptography—also known as asymmetric-key cryptography. This is where each trading partner generates a pair of keys, one of which is public and the other private. Both partners exchange their public keys. Data is encrypted by the sender using the receiver’s public key. Once received the receiver then uses his private key to decrypt the data. DES—this is a single-key system for fast encryption of large volumes of data. The U.S. government regulates this, which means this is only for use within the United States. For international trade outside the U.S., RC2 and RC4 are used. RC2 and RC4—these are single-key systems that can be used instead of DES when one or both trading partners operate outside the U.S. Again because of U.S. government regulations, the key sizes used for the encryption and decryption differ for use within or outside the United States. RSA—this is a public/private key system. Templar SX uses this to add a further level of encryption/decryption and to provide digital signatures. Key sizes that may be used are again different for use within and outside the United States. MIME—multipurpose Internet mail extensions is a standard for formatting messages. PKCS#7—This is the public-key cryptography standard and supports DES, RC2, RC4, RSA algorithms for encryption, decryption and authentication. It also supports message digest (MD5) algorithms for data integrity and the ANSI X.509 standard format for digital certificates.
Useful addressesPremenos Corporation—http://www.premenos.comTemplar SX Demo— http://www.templar.net/cgi-bin/demo.tcl TI Semiconductor EDI— http://www.ti.com/sc/docs/schome.htm Internet Engineering Task Force Internet EDI Draft— http://www.imc.org/draft-ietf-ediint-req EDIFICE—http://www.edifice.org Trade Facilitation Information Exchange— http://www.unece.org/trade/facil/tf_home.htm
Trademarks
Brett Batson |