JAJSGW3D April 2019 – May 2021 CC3235S , CC3235SF
PRODUCTION DATA
- 1 特長
- 2 アプリケーション
- 3 概要
- 4 機能ブロック図
- 5 Revision History
- 6 Device Comparison
- 7 Terminal Configuration and Functions
-
8 Specifications
- 8.1 Absolute Maximum Ratings
- 8.2 ESD Ratings
- 8.3 Power-On Hours (POH)
- 8.4 Recommended Operating Conditions
- 8.5 Current Consumption Summary (CC3235S)
- 8.6 Current Consumption Summary (CC3235SF)
- 8.7 TX Power Control for 2.4 GHz Band
- 8.8 TX Power Control for 5 GHz
- 8.9 Brownout and Blackout Conditions
- 8.10 Electrical Characteristics for GPIO Pins
- 8.11 Electrical Characteristics for Pin Internal Pullup and Pulldown
- 8.12 WLAN Receiver Characteristics
- 8.13 WLAN Transmitter Characteristics
- 8.14 WLAN Transmitter Out-of-Band Emissions
- 8.15 BLE/2.4 GHz Radio Coexistence and WLAN Coexistence Requirements
- 8.16 Thermal Resistance Characteristics for RGK Package
- 8.17
Timing and Switching Characteristics
- 8.17.1 Power Supply Sequencing
- 8.17.2 Device Reset
- 8.17.3 Reset Timing
- 8.17.4 Wakeup From HIBERNATE Mode
- 8.17.5 Clock Specifications
- 8.17.6 Peripherals Timing
- 9 Detailed Description
- 10Applications, Implementation, and Layout
- 11Device and Documentation Support
- 12Mechanical, Packaging, and Orderable Information
9.4 Security
The SimpleLink™ Wi-Fi® CC3235x Internet-on-a chip device enhances the security capabilities available for development of IoT devices, while completely offloading these activities from the MCU to the networking subsystem. The security capabilities include the following key features:
Wi-Fi and Internet Security:
- Personal and enterprise Wi-Fi security
- Personal standards
- AES (WPA2-PSK)
- TKIP (WPA-PSK)
- WEP
- Enterprise standards
- EAP Fast
- EAP PEAPv0/1
- EAP PEAPv0 TLS
- EAP PEAPv1 TLS EAP LS
- EAP TLS
- EAP TTLS TLS
- EAP TTLS MSCHAPv2
- Personal standards
- Secure sockets
- Protocol versions: OCSP, SSL v3, TLS 1.0, TLS 1.1, TLS 1.2
- Powerful crypto engine for fast, secure Wi-Fi and internet connections with 256-bit AES encryption for TLS and SSL connections
- Ciphers suites
- SL_SEC_MASK_SSL_RSA_WITH_RC4_128_SHA
- SL_SEC_MASK_SSL_RSA_WITH_RC4_128_MD5
- SL_SEC_MASK_TLS_RSA_WITH_AES_256_CBC_SHA
- SL_SEC_MASK_TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- SL_SEC_MASK_TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- SL_SEC_MASK_TLS_ECDHE_RSA_WITH_RC4_128_SHA
- SL_SEC_MASK_TLS_RSA_WITH_AES_128_CBC_SHA256
- SL_SEC_MASK_TLS_RSA_WITH_AES_256_CBC_SHA256
- SL_SEC_MASK_TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- SL_SEC_MASK_TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- SL_SEC_MASK_TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- SL_SEC_MASK_TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- SL_SEC_MASK_TLS_RSA_WITH_AES_128_GCM_SHA256
- SL_SEC_MASK_TLS_RSA_WITH_AES_256_GCM_SHA384
- SL_SEC_MASK_TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- SL_SEC_MASK_TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- SL_SEC_MASK_TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- SL_SEC_MASK_TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- SL_SEC_MASK_TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- SL_SEC_MASK_TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- SL_SEC_MASK_TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256
- SL_SEC_MASK_TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
- SL_SEC_MASK_TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256
- Server authentication
- Client authentication
- Domain name verification
- Runtime socket upgrade to secure socket – STARTTLS
- Secure HTTP server (HTTPS)
- Trusted root-certificate catalog – Verifies that the CA used by the application is trusted and known secure content delivery
- TI root-of-trust public key – Hardware-based mechanism that allows authenticating TI as the genuine origin of a given content using asymmetric keys
- Secure content delivery – Allows encrypted file transfer to the system using asymmetric keys created by the device
Code and Data Security:
- Network passwords and certificates are encrypted and signed.
- Cloning protection – Application and data files are encrypted by a unique key per device.
- Access control – Access to application and data files only by using a token provided in file creation time. If an unauthorized access is detected, a tamper protection lock down mechanism takes effect.
- Secured boot – Authentication of the application image on every boot
- Code and data encryption – User application and data files can be encrypted in the serial flash
- Code and data authentication – User Application and data files are authenticated with a public key certificate
- Offloaded crypto library for asymmetric keys, including the ability to create key-pair, sign and verify data buffer
- Recovery mechanism
Device Security:
- Separate execution environments – Application processor and network processor run on separate Arm cores
- Initial secure programming – Allows for keeping the content confidential on the production line
- Debug security
- JTAG lock
- Debug ports lock
- True random number generator
Figure 9-1 shows the high-level structure of the CC3235S and CC3235SF devices. The application image, user data, and network information files (passwords, certificates) are encrypted using a device-specific key.
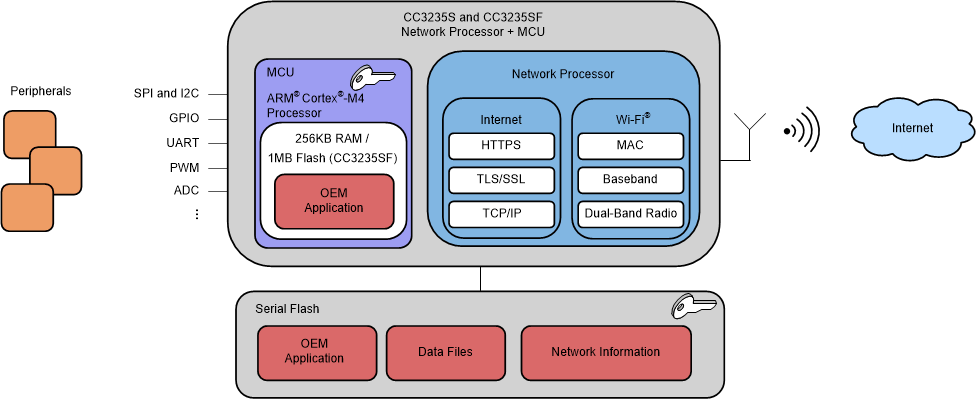 Figure 9-1 CC3235S and CC3235SF High-Level Structure
Figure 9-1 CC3235S and CC3235SF High-Level Structure