SLUAA11B February 2020 – August 2021 BQ769142 , BQ76922 , BQ76942 , BQ76952
- Trademarks
- 1Direct Commands
- 2Subcommands
- 3Reading and Writing RAM Registers
- 4I2C With CRC
-
5SPI
With
CRC Examples
- 5.1 Direct Command Example: Alarm Enable - 0x66
- 5.2 Direct Command Example: Cell 1 Voltage - 0x14
- 5.3 Subcommand Example: Device Number - 0x0001
- 5.4 Subcommand Example: FET_ENABLE - 0x0022
- 5.5 Subcommand Example: RESET - 0x0012
- 5.6 RAM Register Read Example: Enabled Protections A
- 5.7 RAM Register Write Example: Enabled Protections A
- 6Simple Code Examples
- 7References
- 8Revision History
2.1 DEVICE_NUMBER - 0x0001
The device number can be read by first writing the subcommand number 0x0001 (little endian) to the command address 0x3E. This is followed by reading from the data buffer at address 0x40. In this example, the device number returned is 0x7694 (which represents BQ76942).
Table 2-1 DEVICE_NUMBER Subcommand
Description
| Command | Name | Data | Units | Type | Description |
|---|---|---|---|---|---|
| 0x0001 | DEVICE_NUMBER | Device Number | Hex | U2 | Reports the device number that identifies the product. The data is returned in little-endian format |
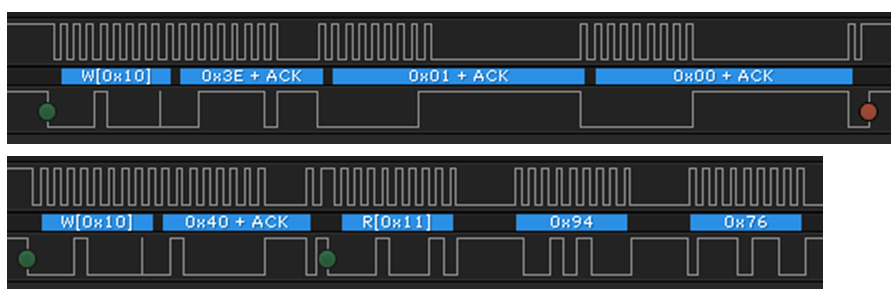 Figure 2-1 Captured I2C Waveform for
DEVICE_NUMBER Subcommand
Figure 2-1 Captured I2C Waveform for
DEVICE_NUMBER Subcommand