SPRUJC1 April 2024
- 1
- Abstract
- Trademarks
- 1Introduction
-
2Steps to Unlock JTAG for HSM Core With
TRACE32
- 2.1 Modifying the SCI Client Default Security Board Configuration
- 2.2 Building the SCI Client Security Board Configuration
- 2.3 Modifying the Secondary Bootloader’s x509 Certificate
- 2.4 Building the Secondary Bootloader
- 2.5 Verifying Secondary Bootloader and TIFS is Executing
- 2.6 Creating a Downloadable x509 Certificate With a Debug Extension
- 2.7 Execution of TRACE32 Unlock Script
- 2.8 Attaching to HSM Core With TRACE32
2.8 Attaching to HSM Core With TRACE32
After successfully executing and unlocking JTAG access for the HSM with the TRACE32 script “J721S2_secure_unlock.cmm”, it is now possible to attach and load HSM symbolic information within TRACE32 for debugging purposes. Please navigate to the following folder location ~/t32/cmm-ti/cmm-dra/cmm-tda4v_j721s2/x_gel_to_cmm/ and edit the following script parameters located in the “_J721S2_m4.cmm” script in order to attach to the HSM (Cortex M4F).
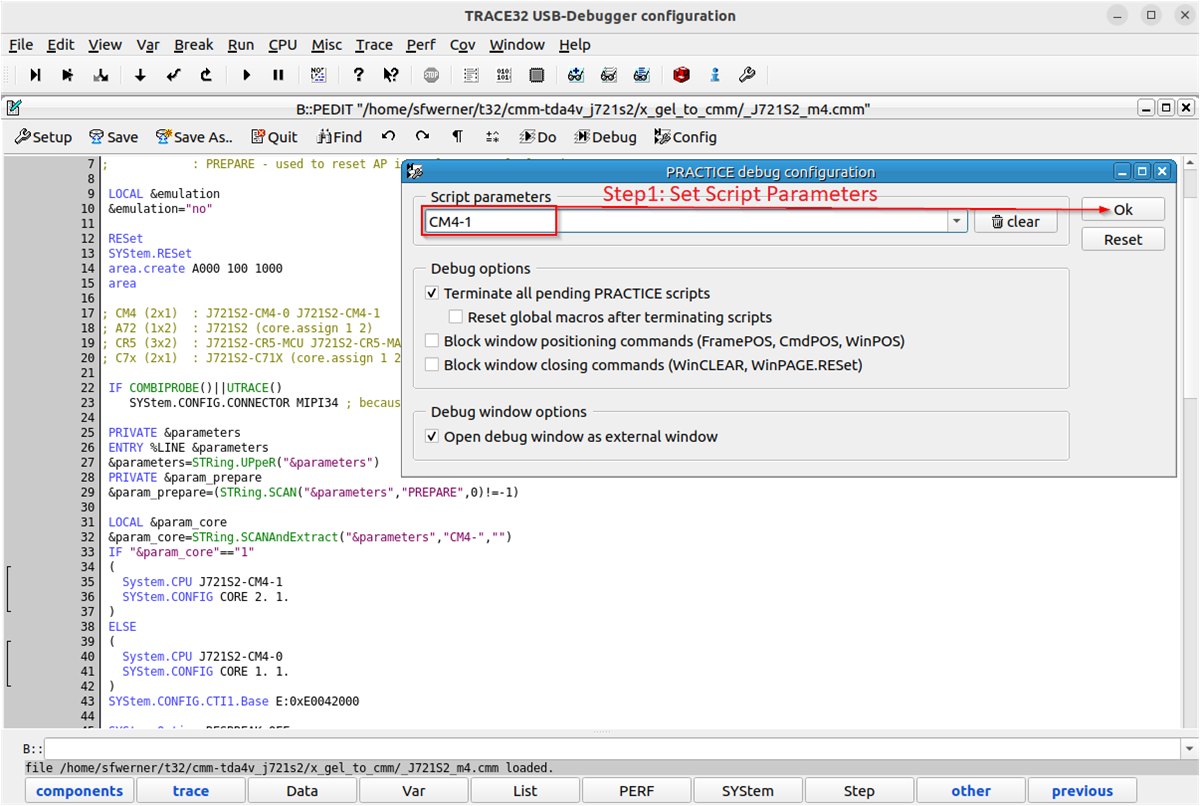 Figure 2-9 TRACE32 – HSM Attach
Script
Figure 2-9 TRACE32 – HSM Attach
ScriptAfter modifying “_J721S2_m4.cmm” script and saving the file, please once again click on the “Do” button in order to execute the script in TRACE32. Finally, you should now be attached to the HSM and able to view debugging windows in TRACE32 as depicted in the Figure 2-10.
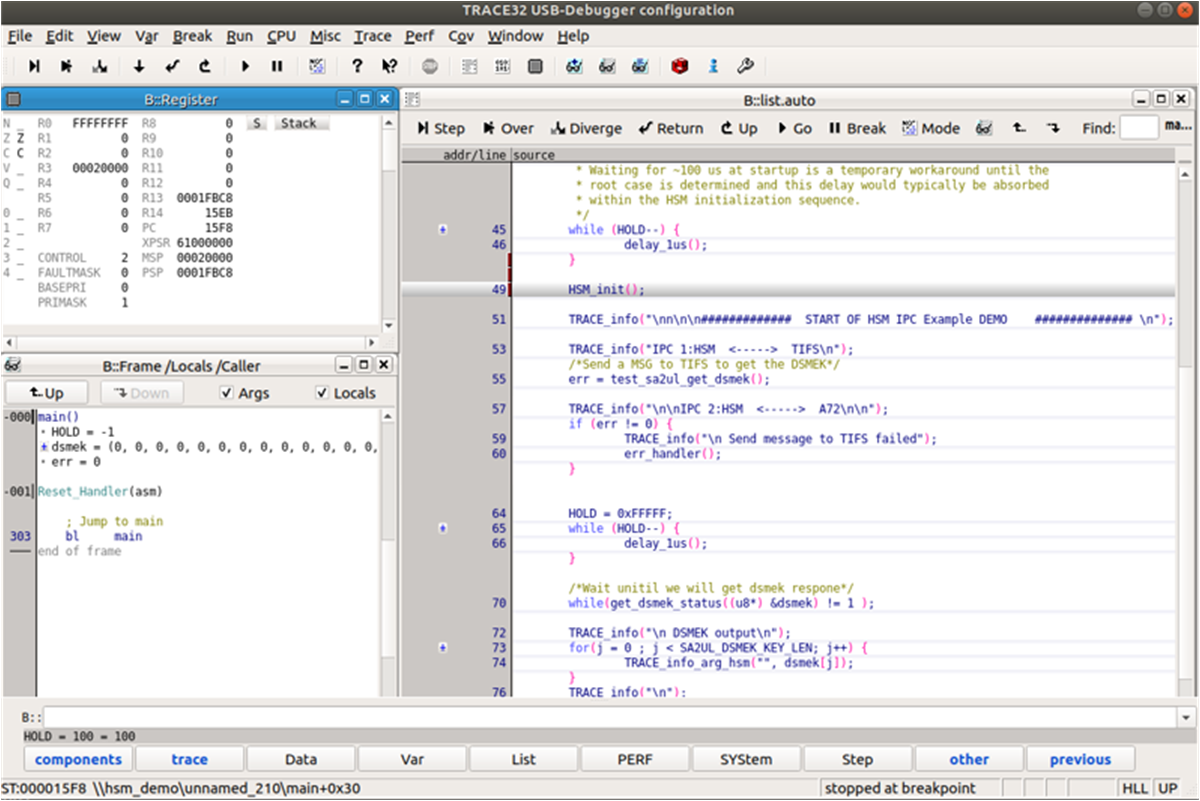 Figure 2-10 TRACE32 – HSM
Debugging
Figure 2-10 TRACE32 – HSM
Debugging