SLAA547C July 2013 – July 2021 MSP430FR5739
4.1.1 Basic Concept of Algorithm
The AES algorithm consists of ten rounds of encryption, as can be seen in Figure 4-1. First the 128-bit key is expanded into eleven so-called round keys, each of them 128 bits in size. Each round includes a transformation using the corresponding cipher key to ensure the security of the encryption.
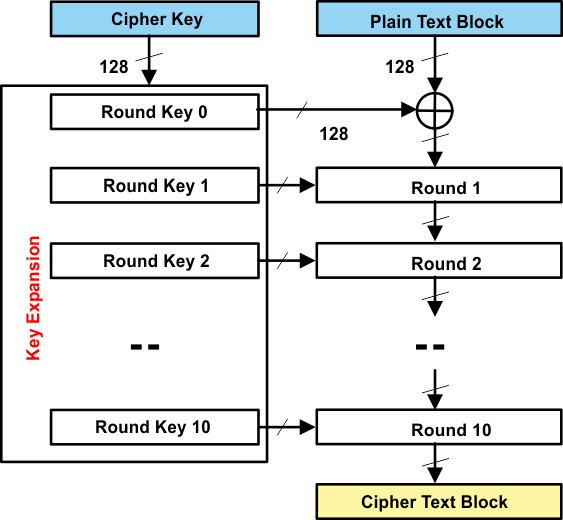 Figure 4-1 AES Algorithm Structure
Figure 4-1 AES Algorithm StructureAfter an initial round, during which the first round key is XORed to the plain text (Add roundkey operation), nine equally structured rounds follow. Each round consists of the following operations:
- Substitute bytes
- Shift rows
- Mix columns
- Add round key
The tenth round is similar to rounds one to nine, but the Mix columns step is omitted. In the following sections, these four operations are explained.