SPRUJC1 April 2024
- 1
- Abstract
- Trademarks
- 1Introduction
-
2Steps to Unlock JTAG for HSM Core With
TRACE32
- 2.1 Modifying the SCI Client Default Security Board Configuration
- 2.2 Building the SCI Client Security Board Configuration
- 2.3 Modifying the Secondary Bootloader’s x509 Certificate
- 2.4 Building the Secondary Bootloader
- 2.5 Verifying Secondary Bootloader and TIFS is Executing
- 2.6 Creating a Downloadable x509 Certificate With a Debug Extension
- 2.7 Execution of TRACE32 Unlock Script
- 2.8 Attaching to HSM Core With TRACE32
2.1.1 PROCESSOR-SDK-RTOS
Located within your PROCESSOR-SDK-RTOS directory, <pdk_path/ti/drv/sciclient/soc/V4/ exists a file named “sciclient_defaultBoardcfg_security.c”. This file contains two structure elements whose values must be configured correctly in order to permit a runtime JTAG unlock to occur.
| Element | Type | Description |
| allow_jtag_unlock | uint8_t | Must be set to 0x5A for runtime JTAG unlock to occur |
| allow_wildcard_unlock | uint8_t | Set to the value of 0 to
enforce UID match before JTAG unlock can occur. Hence the x509
certificate must contain the UID of the device being unlocked. Set to a value of 0x5A to bypass UID match before JTAG unlock. |
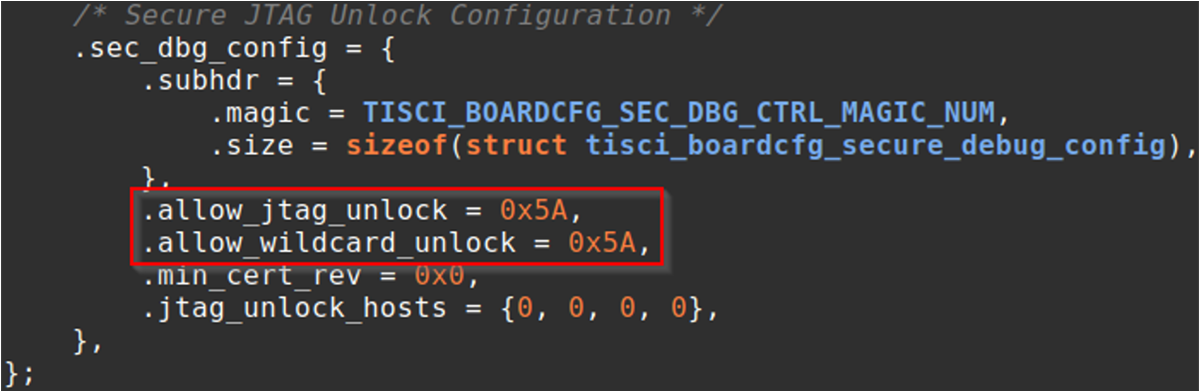 Figure 2-1 Secure Debug Structure –
Example Configuration
Figure 2-1 Secure Debug Structure –
Example ConfigurationIn Figure 2-1, “.allow_jtag_unlock = 0x5A” is set to permit runtime JTAG unlock to occur and “.allow_wildcard_unlock = 0x5A”, which bypasses any UID check before the JTAG unlock. For production use cases, it is recommended to set “.allow_wildcard_unlock = 0x0” in order to enforce the UID check. Enforcing the UID check can prevent the unlocking JTAG of different devices with the same debug certificate.
For a detailed description of all secure debug unlock elements located in the SCI Client Security Board Configuration see TISCI User Guide - Secure Debug Unlock.