SPRUJ12F August 2021 – January 2024 AM2431 , AM2432 , AM2434
- 1
- Abstract
- Trademarks
- 1Preface: Read This First
- 2Kit Overview
- 3Board Setup
-
4Hardware Description
- 4.1 Functional Block Diagram
- 4.2 BoosterPack Headers
- 4.3 GPIO Mapping
- 4.4 Reset
- 4.5 Clock
- 4.6 Memory Interface
- 4.7 Ethernet Interface
- 4.8 USB 2.0 Interface
- 4.9 I2C Interface
- 4.10 Industrial Application LEDs
- 4.11 UART Interface
- 4.12 eQEP Interface
- 4.13 CAN Interface
- 4.14 FSI Interface
- 4.15 JTAG Emulation
- 4.16 Test Automation Interface
- 4.17 SPI Interface
- 5References
- A E3 Design Changes
- B Revision A Design Changes
- Revision History
2.6 Security
The AM243x LaunchPad may have a Non-Secure (GP or General Purpose) or a Secure device (HS-FS). To determine if the device is secure, refer to field parameter for device revision: "r" of the Device name. If the Device Revision is "B" or a subsequent alphabetical letter, then the device is a Secure device.
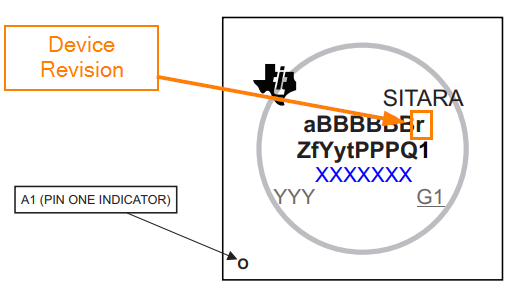 Figure 2-5 Security Field Parameter
Figure 2-5 Security Field ParameterA Secure device has the ability to use a one time programming to convert the device from High Security Field Securable (HS-FS) to High Security Security Enforced (HS-SE).
A secure device leaves the TI factory in an HS-FS state where customer keys are not programmed and has the following attributes:
- Does not enforce the secure boot process
- M3 JTAG port is closed
- R5 JTAG port is open
- Security Subsystem firewalls are closed
- SoC Firewalls are open
- ROM Boot expects a TI signed binary (encryption is optional)
- TIFS-MCU binary is signed by the TI private key
The One Time Programmable (OTP) keywriter converts the secure device from HS-FS to HS-SE. The OTP keywriter programs customer keys into the device eFuses to enforce secure boot and establish a root of trust. The secure boot requires an image to be encrypted (optional) and signed using customer keys, which will be verified by the SoC. A secure device in the HS-SE state has the following attributes:
- M3, R5 JTAG ports are both closed
- Security Subsystem and SoC Firewalls are both closed
- TIFS-MCU and SBL need to be signed with active customer private key