SWRU368C May 2018 – January 2021 CC3100 , CC3100MOD , CC3200 , CC3200MOD
- 1 Overview
- 2 Writing a Simple Networking Application
- 3 Device Initialization
- 4 Device Configurations
- 5 Socket
- 6 Device Hibernate
- 7 Provisioning
- 8 Security
- 9 AP Mode
-
10Peer to Peer (P2P)
- 10.1 General Description
- 10.2 P2P APIs and Configuration
- 10.3 P2P Connection Events
- 10.4 Use Cases and Configuration
- 10.5 Example Code
-
11HTTP Server
- 11.1 Overview
- 11.2 Supported Features
- 11.3 HTTP Web Server Description
- 11.4 HTTP GET Processing
- 11.5 HTTP POST Processing
- 11.6 Internal Web Page
- 11.7 Force AP Mode Support
- 11.8 Accessing the Web Page
- 11.9 HTTP Authentication Check
- 11.10 Handling HTTP Events in Host Using the SimpleLink Driver
- 11.11 SimpleLink Driver Interface the HTTP Web Server
- 11.12 SimpleLink Predefined Tokens
- 12mDNS
- 13Serial Flash File System
- 14Rx Filter
-
15Transceiver Mode
- 15.1 General Description
- 15.2 How to Use / API
- 15.3 Sending and Receiving
- 15.4 Changing Socket Properties
- 15.5 Internal Packet Generator
- 15.6 Transmitting CW (Carrier-Wave)
- 15.7 Connection Policies and Transceiver Mode
- 15.8 Notes about Receiving and Transmitting
- 15.9 Use Cases
- 15.10 TX Continues
- 15.11 Ping
- 15.12 Transceiver Mode Limitations
- 16Rx Statistics
- 17Asynchronous Events
- 18Configurable Info Element
-
19Debug
- 19.1
Capture NWP Logs
- 19.1.1 Overview
- 19.1.2
Instructions
- 19.1.2.1 Configuring Pin Mux for CC32xx
- 19.1.2.2 Terminal Settings
- 19.1.2.3 Run Your Program
- 19.1.2.4
Send to TI Engineer
-
A Host Driver
Architecture
- A.1 Overview
- A.2 Driver Data Flows
-
A Host Driver
Architecture
- 19.1
Capture NWP Logs
15.11 Ping
As an illustration of how a RAW packet is built at the application level. The following demonstrates to build a PING packet encapsulated w/ ICMP, IP and MAC protocols.
- First, there is the PING message
that needs to be transmitted over WLAN PHY.
 Figure 15-5 Ping Data to be
Sent
Figure 15-5 Ping Data to be
Sent - PING is an ICMP QUERY message,
and hence, should first be encapsulated w/ ICMP header.
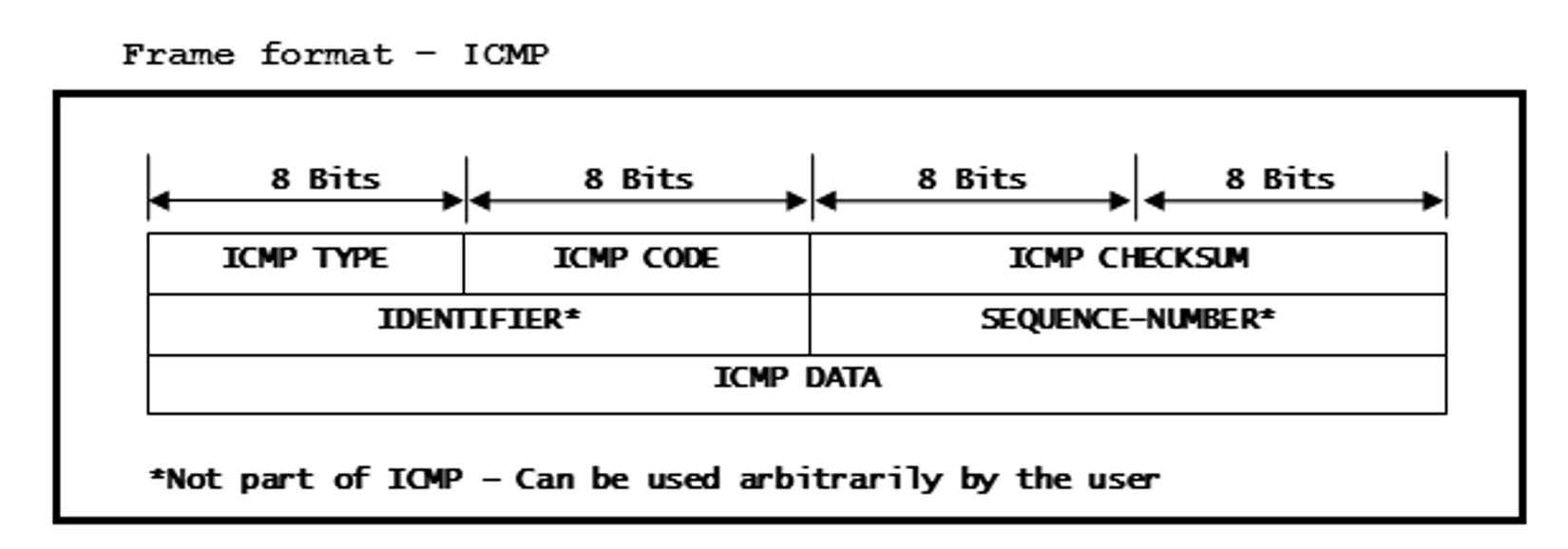 Figure 15-6 Frame Format -
ICMP
Figure 15-6 Frame Format -
ICMP- ICMP TYPE is set to 0x08 since this is an ‘Echo-Request’ message.
- ICMP CODE will always be 0x00 for PING message.
- ICMP CHECKSUM is for header and data and is ‘0xA5, 0x51’ for our message.
- ICMP DATA is “PING data to be sent” defined above.
- Before sending the ICMP
encapsulated PING command to MAC layer, the messages should be encapsulated into
IP data grams. Figure 15-7 shows the frame-format of IPv4 packet.
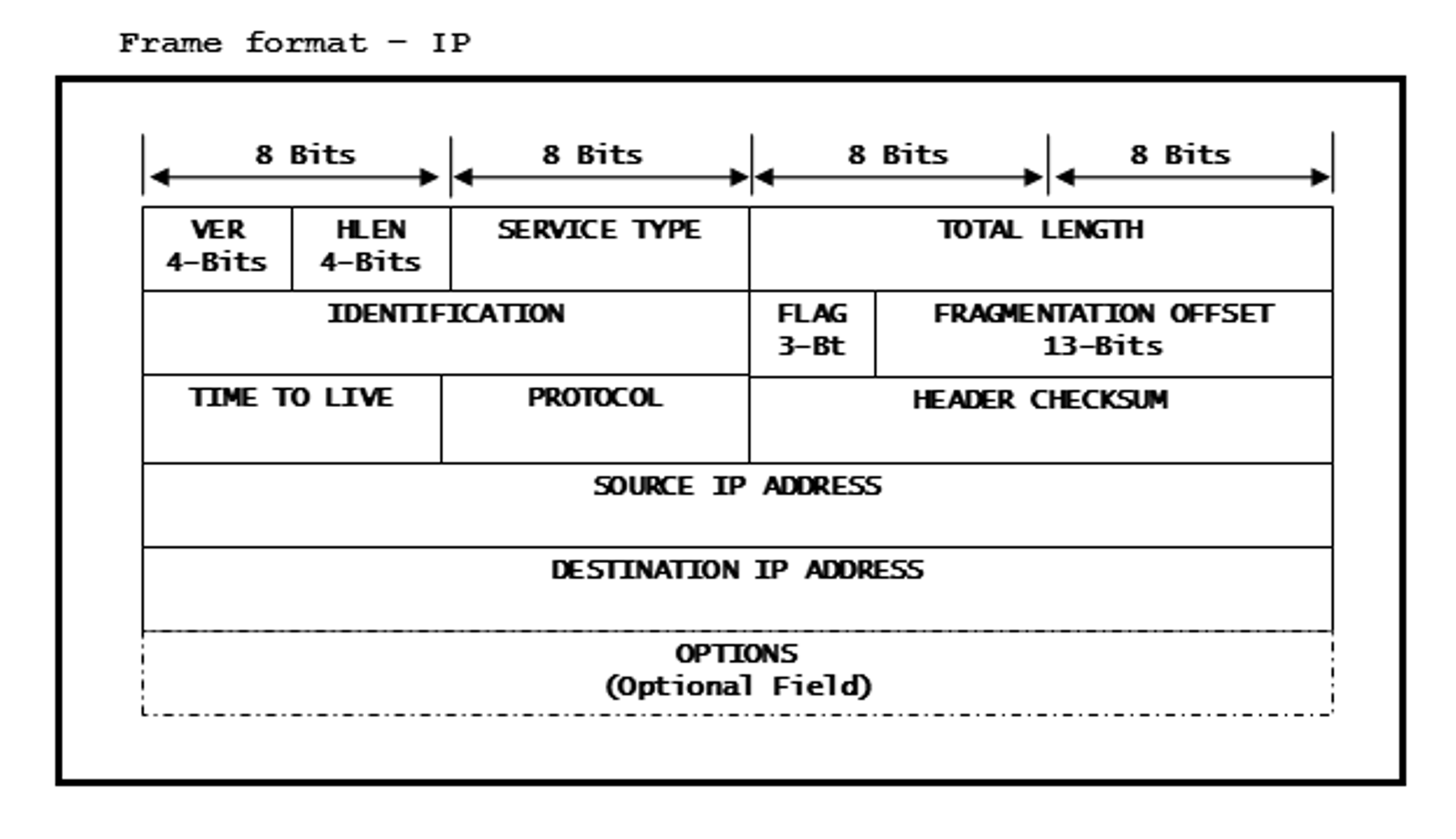 Figure 15-7 Frame Format -
IP
Figure 15-7 Frame Format -
IP- VER is set to 4 since it is a IPv4 packet.
- HLEN is header length in ‘lwords’ - It will be set to 5 here since the header length is 20 Bytes.
- SERVICE TYPE is set to 0x00 since ICMP is a normal service.
- TOTAL LENGTH is set as ‘0x00 0x54’ bytes, which includes header and data length.
- VENDOR ID is set to 0x00, 0x00, 0x00.
- IDENTIFICATION is the unique identity for all data grams sent from this source IP – Let’s set it as ‘0x96, 0xA1’ for our packet.
- FLAG and FRAGMENTATION OFFSET is set to 0x00, 0x00 since there is no intent to fragment the packet. Reason: The packet being sent here is smaller than a WLAN frame size.
- TIME TO LIVE is set to 0x40 because the packet will be discarded after 64 hops.
- PROTOCOL is set to 0x01 since it is an ICMP packet.
- 2 Bytes is HEADER CHECKSUM, which is set to 0x57, 0xFA in this case.
- SOURCE IP ADDRESS is set to 0xc0, 0xa8, 0x01, 0x64 (which is 192.168.1.100).
- DESTINATION IP ADDRESS is set to 0xc0, 0xa8, 0x01, 0x65 (which is 192.168.1.101).
- OPTIONS field is left blank.
- Next, LLC and MAC headers should
be added to the IP encapsulated message. Figure 15-8shows the frame-format of LLC+SNAP header:
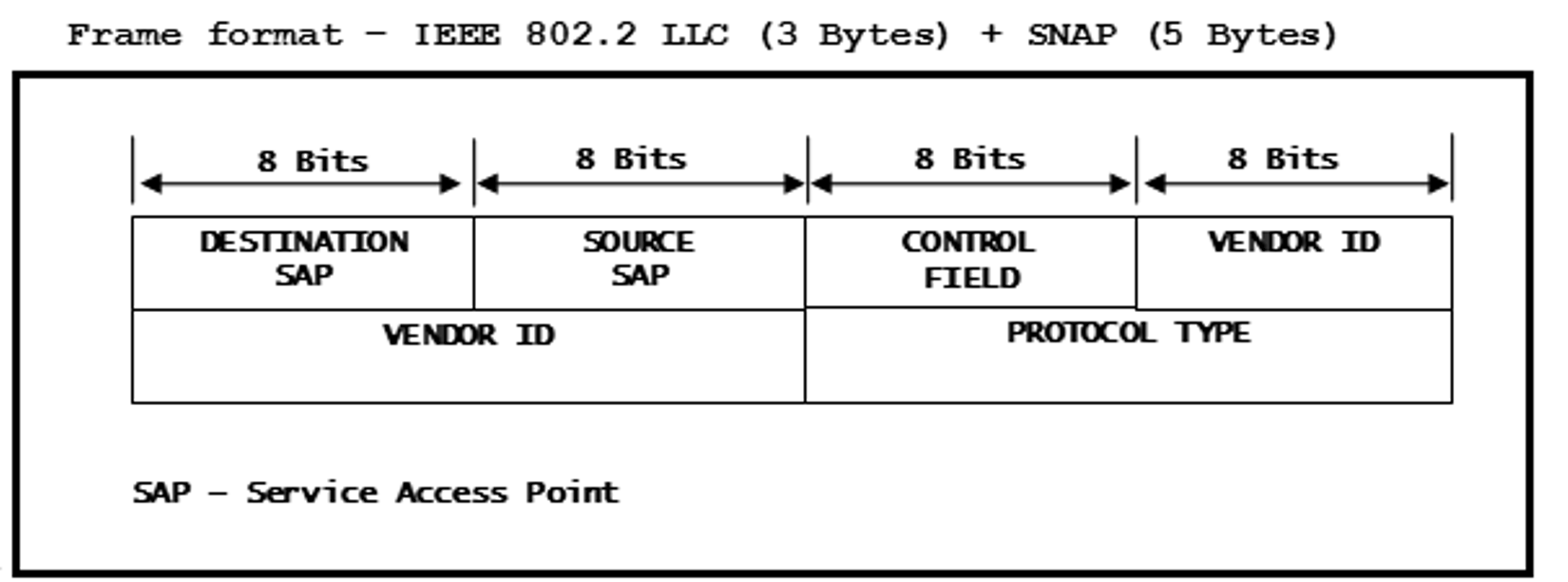 Figure 15-8 Frame Format - IEEE
802.2 LLC (3 bytes) + SNAP (5 bytes)
Figure 15-8 Frame Format - IEEE
802.2 LLC (3 bytes) + SNAP (5 bytes)- DSAP is set to 0xAA to specify that it is a SNAP frame.
- SSAP is set to 0xAA to specify that it is a SNAP frame.
- CONTROL FIELD is set to 0x03 for Sub-Network Access Protocol (SNAP).
- VENDOR ID is set to 0x00, 0x00, 0x00.
- PROTOCOL TYPE is set to 0x08, 0x00 – This is to indicate that the protocol at layer-4 is IP.
- The message is finally
encapsulated with the MAC header. Figure 15-9 shows the frame-format of 802.11 MAC header.
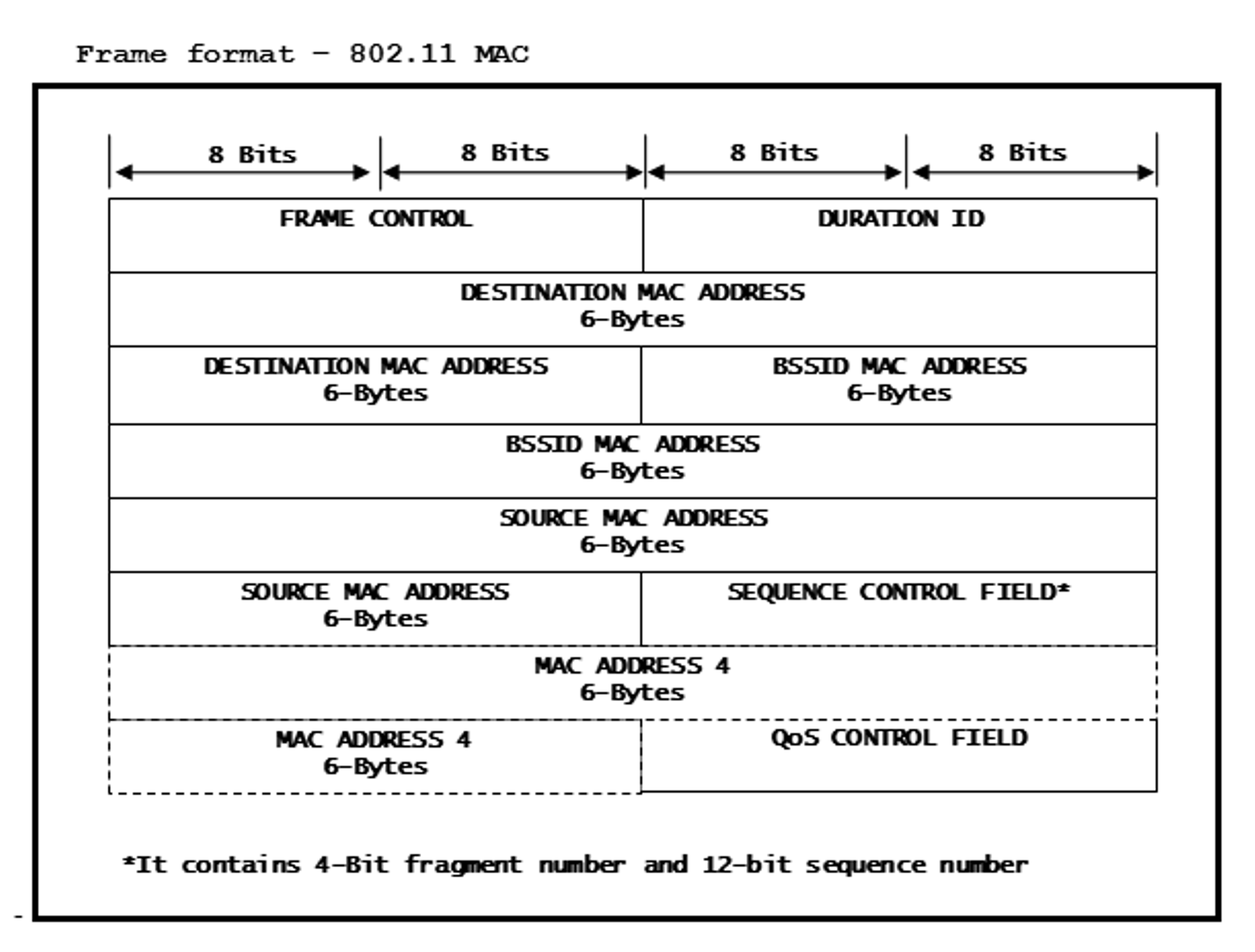 Figure 15-9 Frame Format - 802.11
MAC
Figure 15-9 Frame Format - 802.11
MACFRAME CONTROL is set to 0x88, 0x02 because of below configuration:
- 2-Bits for Protocol Version are set as 00 for 802.11 standard.
- 2-Bits for Type are set as 10 for ‘Data’.
- 4-Bits for Subtype will set as 1000 for ‘QoS Data’.
- Frame Control Field 0x02 is to indicate that the frame is coming from a Distributed-System.
- DURATION ID is set to 44 μS.
- DESTINATION MAC ADDRESS is set to 0x00, 0x23, 0x75, 0x55,0x55, 0x55.
- BSSID MAC ADDRESS is set to 0x00, 0x22, 0x75, 0x55,0x55, 0x55.
- SOURCE MAC ADDRESS is set to 0x00, 0x22, 0x75, 0x55,0x55, 0x55.
- SEQUENCE CONTROL FIELD is
set to 0x42, 0x80.
- Sequence Number is set to 1064 – It is the unique identity for all data grams sent from this source MAC.
- Fragmentation Number is set to 0 – Indicates that there is no fragmentation required.
- The data packet is now
encapsulated with ICMP, IP and MAC headers and is ready to be transmitted over
WLAN PHY. The following is the complete
packet.
RawPingPacket[] = { /*---- 802.11 MAC Header -----*/ 0x88, 0x02, 0x2C, 0x00, 0x00, 0x23, 0x75, 0x55,0x55, 0x55, 0x00, 0x22, 0x75, 0x55,0x55, 0x55, 0x00, 0x22, 0x75, 0x55,0x55, 0x55, 0x80, 0x42, 0x00, 0x00, /*---- LLC & SNAP Header -----*/ 0xAA, 0xAA, 0x03, 0x00, 0x00, 0x00, 0x08, 0x00, /*---- IP Header -----*/ 0x45, 0x00, 0x00, 0x54, 0x96, 0xA1, 0x00, 0x00, 0x40, 0x01, 0x57, 0xFA, 0xc0, 0xa8, 0x01, 0x64, 0xc0, 0xa8, 0x01, 0x65, /*---- ICMP Header -----*/ 0x08, 0x00, 0xA5, 0x51, 0x5E, 0x18, 0x00, 0x00, /*---- Payload -----*/ 0x41, 0x08, 0xBB, 0x8D, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00 }; - To decode the packet, the
received response can be unpacked with the following in mind:
- CC3x00 device will add 8
Bytes of proprietary radio header to the received packet. The header
will have important information about the packet.
- 1 Byte (unsigned char) for RATE: This has rate of data reception.
- 1 Byte (unsigned char) for CHANNEL: This has the channel-number on which the data is received.
- 1 Byte (signed char) for RSSI: It has the computed RSSI value (in dB) of the current frame.
- 1 Byte for PADDING-BITS: It’s for 4B alignment.
- 4 Byte (unsigned long) for TIMESTAMP: Timestamp (in μS) of the received packet. The received messages are tagged with system-time, which by-default starts from 1-1-2000.
- The actual data will follow this 8 Byte header and the application developers should parse it as per their protocol.
- Considering 8 Bytes of
proprietary radio header that gets added to the received packet, 802.11
MAC Header starts from offset-8 of the received packet.
- DESTINATION MAC ADDRESS (6 Byte information) is at offset-4 of 802.11 MAC Header and hence can be extracted starting from offset-12 of received packet.
- SOURCE MAC ADDRESS (6 Bytes information) is at offset-16 of 802.11 MAC Header and, hence, can be extracted starting from offset-24 of received packet.
- Considering 8 Bytes of
proprietary radio header, 26B of MAC header and 8B of LLC & SNAP
header, IP-Header starts from offset-42 of received packet.
- SOURCE IP ADDRESS (4 Byte information) is at offset-12 of ‘IP Header’ and hence can be extracted starting from offset-54 of received packet.
- DESTINATION IP ADDRESS (4 Byte information) is at offset-16 of ‘IP Header’ and, hence, can be extracted starting from offset-58 of received packet.
- The rest of the packet can be decoded as per the next level protocol, and the final decoding code will look like the following:
typedef struct { UINT8 rate; UINT8 channel; INT8 rssi; UINT8 padding; UINT32 timestamp; } TransceiverRxOverHead_t; void TransceiverModeRx (INT8 <channel_number>, INT32 <pkts_to_receive>) { TransceiverRxOverHead_t *frameRadioHeader = NULL; UINT8 buffer[BUFFER_SIZE] = {'\0'}; INT32 <socket_hanlde> = -1; INT32 recievedBytes = 0; <socket_hanlde>= sl_Socket(SL_AF_RF, SL_SOCK_RAW, <channel_number>); while(<pkts_to_receive>--) { memset(&buffer[0], 0, sizeof(buffer)); recievedBytes = sl_Recv(<socket_hanlde>, buffer, BUFFER_SIZE, 0); frameRadioHeader = (TransceiverRxOverHead_t *)buffer; PRINT(" ===>>> Timestamp: %iuS, Signal Strength: %idB\n\r", frameRadioHeader->timestamp, frameRadioHeader->rssi); PRINT(" ===>>> Destination MAC Address: %02x:%02x:%02x:%02x:%02x:%02x\n\r", buffer[12], buffer[13], buffer[14], buffer[15], buffer[16], buffer[17]); PRINT(" ===>>> Source MAC Address: %02x:%02x:%02x:%02x:%02x:%02x\n\r", buffer[24], buffer[25], buffer[26], buffer[27], buffer[28], buffer[29]); PRINT(" ===>>> Source IP Address: %d.%d.%d.%d\n\r", buffer[54], buffer[55], buffer[56], buffer[57]); PRINT(" ===>>> Destination IP Address: %d.%d.%d.%d\n\r", buffer[58], buffer[59], buffer[60], buffer[61]); } sl_Close(<socket_handle>); - CC3x00 device will add 8
Bytes of proprietary radio header to the received packet. The header
will have important information about the packet.