SWPA230A May 2017 – June 2018 CC3120 , CC3120MOD , CC3220MOD , CC3220MODA , CC3220R , CC3220S , CC3220SF
-
CC3120 and CC3220 SimpleLink™ Wi-Fi® Embedded Programming
- Trademarks
- 1 Introduction
- 2 Embedded Programming Schemes
- 3 Setup
- 4 Bootloader Protocol
- 5
Embedded Programming Procedure
- 5.1 Overview
- 5.2 High-Level Flow Diagram
- 5.3
Image Programming in Detail
- 5.3.1 Step 1: Target Connection
- 5.3.2 Step 2: Target Detection
- 5.3.3 Step 3: MUX UART to the Network Processor
- 5.3.4 Step 4: Get SRAM Storage Info
- 5.3.5 Step 5: Raw Storage Erase – SRAM
- 5.3.6 Step 6: Raw Storage Write – SRAM
- 5.3.7 Step 7: Execute from RAM
- 5.3.8 Step 8: Get SFLASH Storage Info
- 5.3.9 Step 9: Raw Storage Erase – SFLASH
- 5.3.10 Step 10: Raw Storage Write – SFLASH
- 5.3.11 Step 11: FS Programming
- 5.3.12 Step 12: Device Reset
- Revision History
5.3.11 Step 11: FS Programming
The next step is the actual programming of the image to the SFLASH. Programming is applied in chunks of 4096 bytes. The image can be either unencrypted or encrypted with a 16-byte symmetric key.
- If the image is unencrypted, the key size is irrelevant and uses a length of 0.
- If the image is encrypted, the key size must be 16 bytes. The key buffer precedes the data chunk.
In both cases, flags are for future use and must be 0. The procedure for programming the SFLASH follows:
- The main processor sends the FS Programming command in chunks of 4096 bytes. The user must provide the following elements in order:
- Key size (in bytes for an encrypted image) must be 16, otherwise 0.
- Chunk size (in bytes) must be 4096, except for the last chunk, which may be smaller according to the residue from the total size.
- Flags must be 0.
- Key buffer
- Data buffer
- The CC3120 or CC3220 device responds with an Ack followed by a 4-byte response indicating the accumulated number of bytes received. The status for the last chunk must be 0 to indicate successful programming, otherwise, a negative status is returned.
- Steps 1 and 2 repeat until the entire image is programmed.
- The image gets extracted and the file system is created.
Figure 15 shows the programming procedure in a zoomed-out pane. The last status code is 0 to indicate a successful programming and is delayed in time to reflect the period of image extraction.
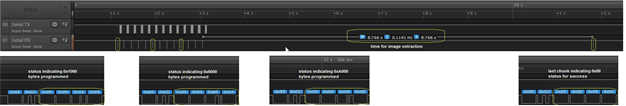 Figure 15. FS Programming (Zoomed Out)
Figure 15. FS Programming (Zoomed Out) Figure 16 shows the programming procedure in a zoomed-in pane for an unencrypted image.
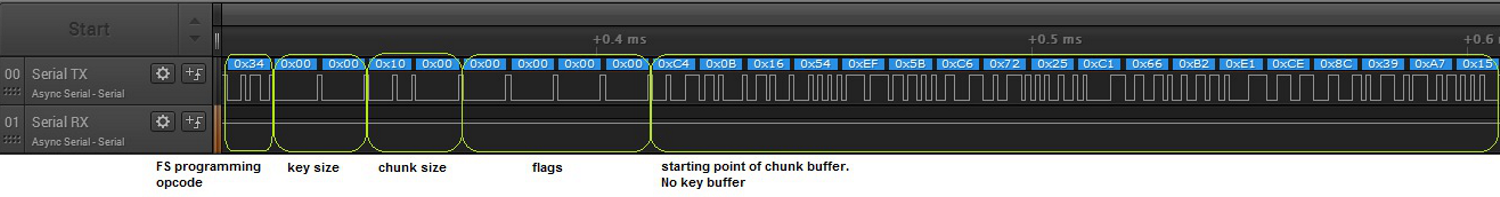 Figure 16. FS Programming of Unencrypted Image (Zoom In)
Figure 16. FS Programming of Unencrypted Image (Zoom In) Figure 17 shows the programming procedure in a zoomed-in pane for an encrypted image.
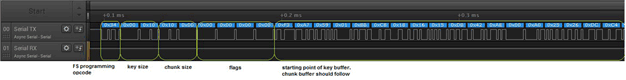 Figure 17. FS Programming of Encrypted Image (Zoomed In)
Figure 17. FS Programming of Encrypted Image (Zoomed In)