SPRACN0F October 2021 – March 2023 F29H850TU , F29H859TU-Q1 , TMS320F280021 , TMS320F280021-Q1 , TMS320F280023 , TMS320F280023-Q1 , TMS320F280023C , TMS320F280025 , TMS320F280025-Q1 , TMS320F280025C , TMS320F280025C-Q1 , TMS320F280033 , TMS320F280034 , TMS320F280034-Q1 , TMS320F280036-Q1 , TMS320F280036C-Q1 , TMS320F280037 , TMS320F280037-Q1 , TMS320F280037C , TMS320F280037C-Q1 , TMS320F280038-Q1 , TMS320F280038C-Q1 , TMS320F280039 , TMS320F280039-Q1 , TMS320F280039C , TMS320F280039C-Q1 , TMS320F280040-Q1 , TMS320F280040C-Q1 , TMS320F280041 , TMS320F280041-Q1 , TMS320F280041C , TMS320F280041C-Q1 , TMS320F280045 , TMS320F280048-Q1 , TMS320F280048C-Q1 , TMS320F280049 , TMS320F280049-Q1 , TMS320F280049C , TMS320F280049C-Q1 , TMS320F28374D , TMS320F28374S , TMS320F28375D , TMS320F28375S , TMS320F28375S-Q1 , TMS320F28376D , TMS320F28376S , TMS320F28377S , TMS320F28377S-Q1 , TMS320F28378D , TMS320F28378S , TMS320F28379D , TMS320F28379D-Q1 , TMS320F28379S , TMS320F28384D , TMS320F28384S , TMS320F28386D , TMS320F28386S , TMS320F28388D , TMS320F28388S , TMS320F28P650DH , TMS320F28P650DK , TMS320F28P650SH , TMS320F28P650SK , TMS320F28P659DH-Q1 , TMS320F28P659DK-Q1 , TMS320F28P659SH-Q1
- The Essential Guide for Developing With C2000™ Real-Time Microcontrollers
- Trademarks
- 1C2000 and Real-Time Control
-
2Sensing Key Technologies
- 2.1 Accurate Digital Domain Representation of Analog Signals
- 2.2 Optimizing Acquisition Time vs Circuit Complexity for Analog Inputs
- 2.3 Hardware Based Monitoring of Dual-Thresholds Using a Single Pin Reference
- 2.4 Resolving Tolerance and Aging Effects During ADC Sampling
- 2.5 Realizing Rotary Sensing Solutions Using C2000 Configurable Logic Block
- 2.6 Smart Sensing Across An Isolation Boundary
- 2.7 Enabling Intra-Period Updates in High Bandwidth Control Topologies
- 2.8 Accurate Monitoring of Real-Time Control System Events Without the Need for Signal Conditioning
-
3Processing Key Technologies
- 3.1 Accelerated Trigonometric Math Functions
- 3.2 Fast Onboard Integer Division
- 3.3 Hardware Support for Double-Precision Floating-Point Operations
- 3.4 Increasing Control Loop Bandwidth With An Independent Processing Unit
- 3.5 Flexible System Interconnect: C2000 X-Bar
- 3.6 Improving Control Performance With Nonlinear PID Control
- 3.7 Understanding Flash Memory Performance In Real-Time Control Applications
- 3.8 Deterministic Program Execution With the C28x DSP Core
- 3.9 Efficient Live Firmware Updates (LFU) and Firmware Over-The-Air (FOTA) updates
-
4Control Key Technologies
- 4.1 Reducing Limit Cycling in Control Systems With C2000 HRPWMs
- 4.2 Shoot Through Prevention for Current Control Topologies With Configurable Deadband
- 4.3 On-Chip Hardware Customization Using the C2000 Configurable Logic Block
- 4.4 Fast Detection of Over and Under Currents and Voltages
- 4.5 Improving System Power Density With High Resolution Phase Control
- 4.6 Safe and Optimized PWM Updates in High-Frequency, Multi-Phase and Variable Frequency Topologies
- 4.7 Solving Event Synchronization Across Multiple Controllers in Decentralized Control Systems
- 5Interface Key Technologies
- 6Safety Key Technologies
- 7References
- 8Revision History
3.8.2 In Depth
A processor that is not consistent in its behavior over time can cause perturbations to a real-time control system, either by not actuating the system in a timely manner or by sampling the state of the system at the incorrect point in time. Furthermore, real-time control systems are largely interrupt driven in their program flow. For this reason, a cache memory is undesirable since it would need to be discarded often whenever a program discontinuity occurs (in this case quite often).
Instead, large amounts of fast memory are desirable for program execution as well as a processor with a instruction pipeline that is deep enough to parallelize instructions, but also shallow enough to not incur large time penalties when discontinuities occur. The C28x CPU employees an 8 stage pipeline as shown in #T5843526-197. Once an instruction has entered the D2 phase of the pipeline, it cannot be stopped from full execution by an interrupt. Conversely, any instruction that is in a pre-D2 phase of the pipeline will be flushed when the incoming interrupt is received by the C28x core. Upon returning from the interrupt program, execution begins again with the F1 fetch stage. It is beyond the scope of this article to go deeper into the nuances of the pipeline, but those details are covered in the TMS320C28x DSP CPU and Instruction Set Reference Guide.
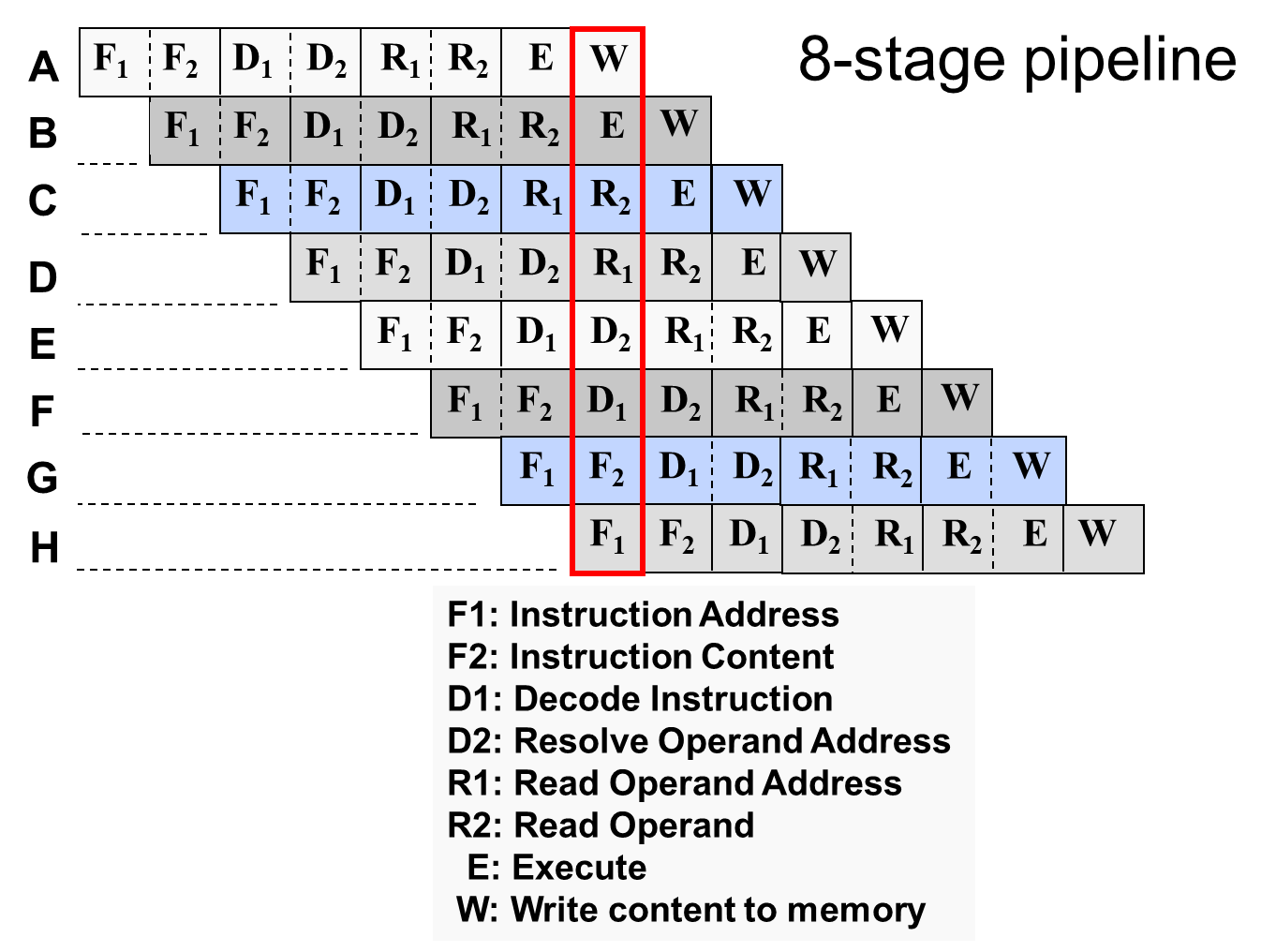 Figure 3-13 C28x Pipeline
Visualization
Figure 3-13 C28x Pipeline
VisualizationWhile you can see that the behavior of the program execution is repeatable over time, what about the behavior of the incoming interrupt? #T5843526-193 shows that this, too, is deterministic. Note that unless manually altered all other interrupt requests will pend until the current interrupt has been fully serviced. This is important in order to keep servicing of any interrupt consistent in the time domain once it begins. Both of these components of the C28x core help maintain deterministic code execution for the system.
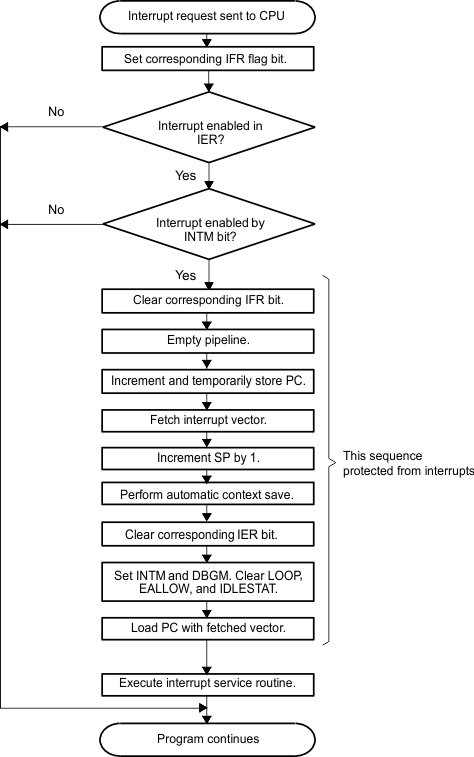 Figure 3-14 Standard Operation for a C28x
CPU Maskable Interrupt
Figure 3-14 Standard Operation for a C28x
CPU Maskable Interrupt